
Breaking News
 Chinese freighter halves EU delivery time on maiden Arctic voyage to UK
Chinese freighter halves EU delivery time on maiden Arctic voyage to UK
 Alex Jones Warns of the Globalist Death Cult Fueling the Next Civil War and Rise of the Antichrist
Alex Jones Warns of the Globalist Death Cult Fueling the Next Civil War and Rise of the Antichrist
 Is Donald Trump Intent Upon Imposing Martial Law in America?
Is Donald Trump Intent Upon Imposing Martial Law in America?
 Must-See Report! NATO Claims Putin Preparing To Attack Europe As Russia Enters 'Phase Zero'
Must-See Report! NATO Claims Putin Preparing To Attack Europe As Russia Enters 'Phase Zero'
Top Tech News
SEMI-NEWS/SEMI-SATIRE: October 12, 2025 Edition
 Stem Cell Breakthrough for People with Parkinson's
Stem Cell Breakthrough for People with Parkinson's
 Linux Will Work For You. Time to Dump Windows 10. And Don't Bother with Windows 11
Linux Will Work For You. Time to Dump Windows 10. And Don't Bother with Windows 11
 XAI Using $18 Billion to Get 300,000 More Nvidia B200 Chips
XAI Using $18 Billion to Get 300,000 More Nvidia B200 Chips
 Immortal Monkeys? Not Quite, But Scientists Just Reversed Aging With 'Super' Stem Cells
Immortal Monkeys? Not Quite, But Scientists Just Reversed Aging With 'Super' Stem Cells
 ICE To Buy Tool That Tracks Locations Of Hundreds Of Millions Of Phones Every Day
ICE To Buy Tool That Tracks Locations Of Hundreds Of Millions Of Phones Every Day
 Yixiang 16kWh Battery For $1,920!? New Design!
Yixiang 16kWh Battery For $1,920!? New Design!
 Find a COMPATIBLE Linux Computer for $200+: Roadmap to Linux. Part 1
Find a COMPATIBLE Linux Computer for $200+: Roadmap to Linux. Part 1
 Bionic hand with NO brain implants?!
Bionic hand with NO brain implants?!
 Nano-cubosome eyedrops target macular degeneration without needles
Nano-cubosome eyedrops target macular degeneration without needles
This 'Demonically Clever' Backdoor Hides In a Tiny Slice of a Computer Chip
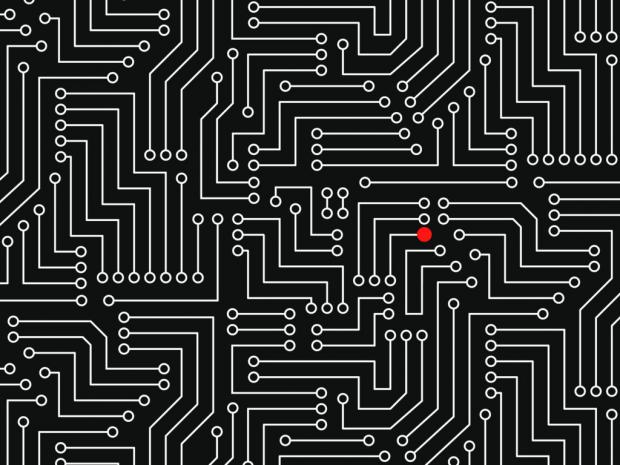
Now imagine a backdoor planted not in an application, or deep in an operating system, but even deeper, in the hardware of the processor that runs a computer. And now imagine that silicon backdoor is invisible not only to the computer's software, but even to the chip's designer, who has no idea that it was added by the chip's manufacturer, likely in some farflung Chinese factory. And that it's a single component hidden among hundreds of millions or billions. And that each one of those components is less than a thousandth of the width of a human hair.
In fact, researchers at the University of Michigan haven't just imagined that computer security nightmare; they've built and proved it works. In a study that won the "best paper" award at last week's IEEE Symposium on Privacy and Security, they detailed the creation of an insidious, microscopic hardware backdoor proof-of-concept. And they showed that by running a series of seemingly innocuous commands on their minutely sabotaged processor, a hacker could reliably trigger a feature of the chip that gives them full access to the operating system. Most disturbingly, they write, that microscopic hardware backdoor wouldn't be caught by practically any modern method of hardware security analysis, and could be planted by a single employee of a chip factory.



